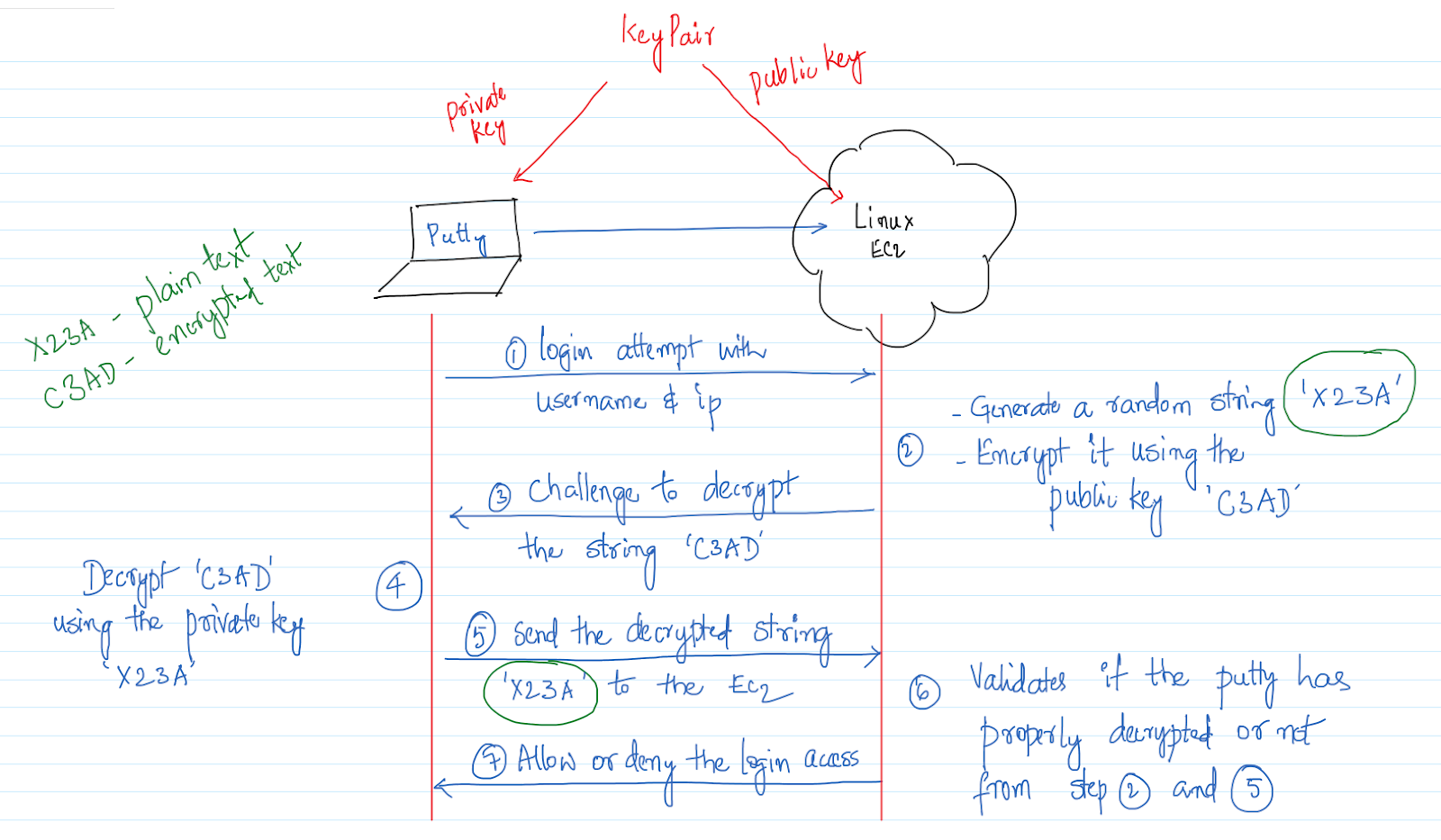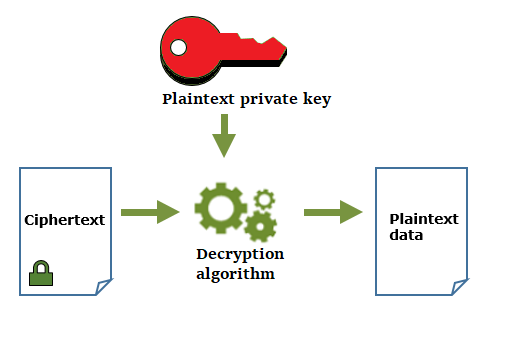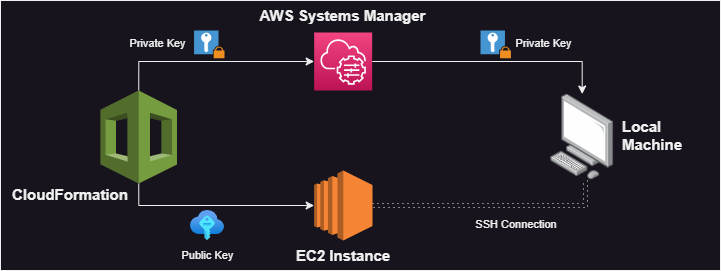
Get Private SSH Key after Creating Key Pair with AWS CloudFormation — Quick Tip/Bash Script | by tope | Medium

How to migrate symmetric exportable keys from AWS CloudHSM Classic to AWS CloudHSM | AWS Security Blog

amazon ec2 - From a running EC2 instance, how do I download the AWS generated private key for use with SSH and WinSCP? - Server Fault
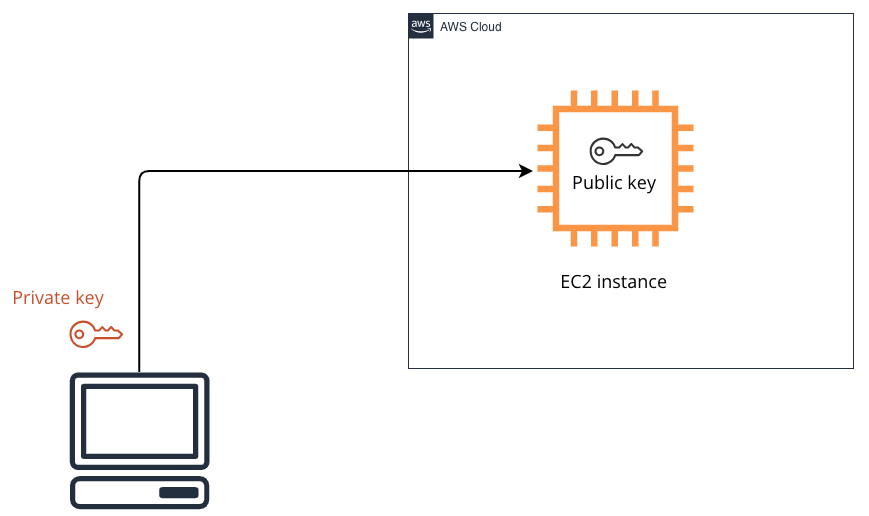
Recover Access to EC2 Linux Instance After Losing KeyPair | by Ahmed Mansouri | AWS in Plain English

Use Key Management Service (AWS KMS) to securely manage Ethereum accounts: Part 1 | AWS Database Blog